Q/SA® Qualified/ Security Analyst Penetration Tester (non-degree certification)
& Q/PTL® Workshop in 5 days!
Hands DOWN! The Best Pen Testing Certification! says USAF Red team
There are other Pen Testing Licenses out there, but none validate your "Qualified" than SU's Q/PLT, says NASA.
 The Q/SA- Q/PTL Qualified/ Security Analyst Penetration Tester certification class & Q/PTL Qualified/ Penetration Tester License validation lab prepares you to learn CNSS 4011, 4012, 4016A RED TEAM Training. It's"how to do Vulnerability Analysis" & "how to report" how compromised the network can be. You learn SU's Vulnerability Analysis & Penetration Testing process and methodology while doing "no harm".
The Q/SA- Q/PTL Qualified/ Security Analyst Penetration Tester certification class & Q/PTL Qualified/ Penetration Tester License validation lab prepares you to learn CNSS 4011, 4012, 4016A RED TEAM Training. It's"how to do Vulnerability Analysis" & "how to report" how compromised the network can be. You learn SU's Vulnerability Analysis & Penetration Testing process and methodology while doing "no harm".
The majority of the class consists of probing target networks, gaining user-level access and demonstrating just how compromised the network can be. SU teaches you the red team skills like leaving an innocuous file on a secure part of a network as a calling card, as if to say, “This is your friendly red team. We danced past the comical precautionary measures you call security hours ago. This file isn't doing anything, but if we were anywhere near as evil as the hackers we're simulating, it might just be deleting the very secrets you were supposed to be protecting. Have a nice day!”
How does SANS SEC560: Network Penetration and Ethical Hacking Course Different from the Q/SA - Q/PTL Qualified/Security Analyst vs CEH Certified Ethical Hacker Course?
Below is a comparison of these three penetration testing & hacking courses:
SANS Network Penetration Testing vs Q/SA- Q/PTL vs CEH (Certified Ethical Hacker) |
|||
Topics |
SANS |
CEH |
Q/SA Q/PTL |
Provides an entry-level knowledge of penetration testing |
-- |
X |
X |
Provides an step by step process and methodology of Penetration Testing |
-- |
-- |
X |
Develops security testing skills using live pen testing target range |
X |
-- |
X |
Analyzes how penetration testing and ethical hacking fit into a qualified information security program |
-- |
-- |
X |
Focuses on skill development and provides in-depth, technical skills for experienced pen testers |
X |
-- |
X |
Provides in-depth understanding of the most powerful and useful pen testing tools and how they interrelate |
X |
-- |
X |
Addresses real-world strategies and tactics to avoid common pen test pitfalls and maximize efficiency of testing |
X |
-- |
|
Discusses how to define appropriate rules of engagement and build a pen test project scope |
X |
-- |
X |
Focuses on penetration test workflow and step-by-step methods for conducting projects |
X |
-- |
X |
Learns how to do pen testing step by step with secrets from industry experts |
-- |
-- |
X |
Emphasizes the mindset of successful penetration testing and ethical hacking, including troubleshooting, weighing risks, following a proven process, documentation, and final reports based on business risk |
X |
-- |
X |
Covers techniques for maximizing the value of a pen test through thorough reporting and business focus |
X |
-- |
X |
Ensures experienced instructors with real-world pen testing experience |
X |
-- |
X |
Culminates in a hands-on penetration test of an example target organization modeling real-world security flaws |
X |
-- |
X |
Qualifies and validate the penetration tester skills based on a 3 hr live penetration test compete with report back to management. ( since 1999) |
-- |
-- |
X |
The Q/SA® - Q/PTL® is the only performance based security skills assessment certification that validates your Qualified/ Security Analyst Penetration Tester skills.
What is SUT Q/ISP Certificate?
SUT Q/ISP Certification is obtained through SU for the purpose of recognizing qualified individuals who have distinguished themselves as knowledgeable and proficient information security practitioners with validated hands-on cybersecurity skills. The SUT Q/ISP certificate identifies certified ying qualified persons who subscribe to a rigorous requirement for maintaining their knowledge and proficiency in information security with "validated" their hands-on tactical security skills.
 Certification is awarded to those qualified individuals who validate their security skills to a prescribed qualified level of tactical hands-on information security experience, comply with a professional code of ethics, and pass rigorous examinations on the Q/ISP Body of Knowledge for information security.
Certification is awarded to those qualified individuals who validate their security skills to a prescribed qualified level of tactical hands-on information security experience, comply with a professional code of ethics, and pass rigorous examinations on the Q/ISP Body of Knowledge for information security.
Keeping your Q/ISP Valid
In order to maintain currency in the field, each Q/ISP must complete participation in research or study, attendance at recognized subject-matter training and professional educational programs, presentation or publication of information security papers, contributions to the information security Q/ISP Body of Knowledge, or service in professional organizations. Each Q/ISP must acquire 216 CPE continuing professional education credits every three years. (72 credits per year)
In order to use a Qualified Q/ISP Trustmark the Q/ISP has validated their tactical security skills by completing the Tactical Security Certification Practical's from the Q/PTL, Q/FE & Q/ND classes.
| Class Fee | $2,995 + 1/2 price for Q/PTL( $1,500 off !) $4,500 for class+ Practical | <
| Time: | 7:45 am 4pm, 4pm --8 pm (4 hr labs Tues- Thur) |
| Location: | Click here to view the class schedule |
| Prerequisites: | Understanding of TCP/IP protocols |
| CPE Credits: | 72 Q/SA + 30 for Q/PTL |
| Instructor: | Highly qualified instructor with CEH™/ Q/EH®, Q/SA® Q/SA EXAM Vouchers incl in class fee |
Method of Delivery - Residential On Ground
Method of Evaluation: 1. 95 % attendance 2. 100 % completion of Lab
Grading: Pass = 95% Attendance and 100% Completion of Labs and Practical
Fail => 95% Attendance and > 100% Completion of Labs and Practical

CORE IMPACT from Core Security 8IP, 7-day eval LICENSE with every class registration! a $25,000 value - only at Security University!

Who should attend:
- System and Network Administrators
- Security Personnel
- Auditors
- Consultants concerned with network security
- Threat management team
- Software programmers
- Forensic experts

Download the SU Computer Security Class Roadmap
Qualified Training for Qualified Results
Q/SA® Qualified/ Security Analyst Penetration Tester class & Q/PTL® License is much higher on the security pyramid of Security Analysis & Network Penetration Testing Skills Classes and Certifications. We set the bar to provide you tactical security skills including:
- Security Analysis and Penetration Testing Process & Methodology
- Latest exploit goals and methodologies
- Understanding the mind set needed to perform penetration testing
- Advanced information-gathering techniques
- Expert network discovery tools and techniques
- Identifying & exploiting network weaknesses with Core Impact and more tools
- Advanced enumeration of network devices, platforms and protocols
- Cracking contemporary authentication and authorization
- Advanced router, firewall and IDS testing \ Exploiting IPS
- Vulnerability research and automated scanning in the enterprise
- Exploits & tools
- Scanning for root kits, trojans, malware and viruses
- Tools for web application testing - Watchfire Appscan and freeware tools
- Exploiting complex protocols, such as SSH, SSL, and IPSEC
- Using payload generators
- Advanced wireless testing tools and techniques
- Advanced wireless testing tools and techniques AirCrack-NG
- Penetration testing and the law
You'll learn how to gather viable data on your network & network vulnerabilities using leading edge tools like Nessus , GFI Landguard and Hyena, SOLAR WIND S, NMAP. During your testing you will learn how to use Exploitation tools like MetaSploit, Saint Scanner / SaintExploit tool , CORE IMPACT from Core Security, NIKTO & Open Source tools.
Penetration concepts you will master during this hands on class
|
|
Instructor-led hands-on lab exercises
|
|
Phase I — Gather the Data
A first look at a network site, from the eyes of a potential hacker. The simple, and often overlooked, things that tell hackers if a site is worth a penetration attempt.
Phase II — Penetrate the Network
How hackers get past the security and into the data.
- Non-intrusive target search
- Intrusive target search
- Data analysis
Network Discovery Tools and Techniques: Hands-On Exercises
- Discovery/profiling objectives
- Locating Internet connections
- Host-locating techniques: manual and automated
- Operating system footprinting
- Evaluating Windows and Unix-based network discovery software tools
- Evaluating Windows and Unix-based application scanning software tools
- Review Step-by-step process of each scanning and profiling tool
- Directory services: DNS, DHCP, BOOTP, NIS
- Look-up services: finger, whois, search engines
- Remote sessions: telnet, "r" commands, X-Windows
- File sharing and messaging: FTP, TFTP, World Wide Web
- Windows Server Message Block (SMB), Network File
- Systems (NFS), and e-mail
- Sample exploits using common TCP/IP and NetBIOS utility software
The Q/SA® & Q/PTL® materials address common pitfalls in penetration testing and ethical hacking projects, with real-world targets and to maximize the quality of test results. Daily complex scenarios and capture the flag exercises increase your tactical skills.
- Learn timesaving tactics based on years of tactical security experiences from real penetration testers and ethical hackers defeating a problem in minutes.
- We stress the mind-set of successful penetration testers and ethical hackers and balance skills with "outside-the-box" thinking, a penetration methodology that stands the test of time and carefully weighing risks, and creating a quality final report for management
- You analyze how penetration testing and ethical hacking fits into a comprehensive information security & assurance program.
Phase III — Analyze the Results
Tips and techniques for effective, actionable penetration test analysis.
- Identifying network services
- Pinpointing vulnerabilities
- Demonstrating risks and escalating permissions
- Reviewing reports and screens from prominent discovery/profiling tools
- Analyzing current configuration
Real-World Scenarios
- Abusive e-mail
- Embezzlement
- Pornography
- Denial-of-service
- Web defacement
- Trojan Horse
Phase IV — Write the Report
How to combine methodology, results, and analysis into a report that generates management attention and buy-in… and provides clear, workable action items.
In-Class Exercises for your Q/PTL® Validation "Qualification"
- Building and maintaining a target list
- Conducting multiple non-intrusive and intrusive target searches
- Tools and techniques for testing for Web site vulnerabilities
- Probing and attacking network firewall's
- Performing multiple remote target assessment
- Performing multiple host assessment
- Validating vulnerabilities
- Writing up the final report
- Prepares you for the Q/PTL validation " Practical" Exam
10 years ago Security University started training security professionals with the very best penetration step by step process and methodology class, SU is still the leader in security Analysis & Penetration Testing Certifications in the industry. Security University Q/SA® class is CNSS-approved.
Now you can take the same Penetration Testing process and methodology class that trains the US Air Force, Army, Navy and Marines trained to defend military networks. Your class is taught by SSME (Security Subject Matter Experts) who know the "Art of Penetration Testing & Hacking". You'll gain serious tactical security skills that will set you apart from your peers.
As an Army Information Systems Management (FA53) officer focusing on Cyber Defense, I've had the opportunity to train and certify in several IA/CND specific programs as well as work a myriad of Army Cyber Defense workforce training and development issues.
Having just recently completed the Security University (SU) Qualified Security Analyst (Q|SA) and Qualified Penetration Tester License (Q|PTL) courses I can confidently say that Sondra and her team have built an exceptional program of instruction; capturing the essential elements of security analysis and penetration testing methodologies and delivering them in a clear and concise format in a blended learning environment of lecture and hands-on practical skill development with scenario-based final examinations. SU training techniques are a perfect match for our military cyber defense workforce goals since they not only train the relevant concepts of cyber defense and its CND specialties but also in the case of Q|SA and Q|PTL courses challenge the students to apply those concepts in a "tactical" setting that an actual security analyst or penetration tester might see.
Security University's Q|SA / Q|PTL program of instruction is impressive and superior to some other training programs in several ways; one of them being the daily hands-on assessment of critical skills being taught. Another was the realistic practical final exam which included a penetration test with a final report that required some in-depth analysis of the resulting sets of data. I spent 30 post-course hours alone on analyzing the data and developing a 32 page report. That's definitely an experience you're not going to get through other training programs that teach a five day curriculum that's predominately lecture based. The Q|SA and Q|PTL courses also expose the students to a wide range of open and closed source automated tools for use in security analysis and penetration testing as well as the built-in assessment and exploitation capabilities of both Linux and Windows based operating systems. I honestly can't understand how we expect to conduct defense in depth across the GiG without our technical workforce understanding basic exploitation, which is exactly what's missing from many other approved certifications. SU equally balances this with methodology and analysis techniques rather than relying on specific toolsets since tools frequently change and are always subject to interpretation of their results.
Appendix I,II,III
Packet Filtering,
IDS Log Analysis,
Vulnerability,
Log Analysis,
IPS & IDS correlation,
IDS & IPD countermeasures,
Wireless Security,
Software Security,
Network Security,
Event Correlation,
Threat Mgt,
Security Polices,
Virus Malware,
Code Review,
Reverse Engineering,
COOP,
Incident Response,
C&A
What is a Q/ISP® "Qualified" Information Security Professional Certification?
The 125 question online Q/ISP certification exam has questions from 4 Q/ISP Security Skills certification prep classes:
Qualified/Ethical Hacking
Qualified/Security Analysis Penetration Testing
Qualified/Forensics Expert
Qualified/Network Defense
The Q/ISP, Q/EH, Q/SA- Q/PTL, Q/FE & Q/ND certification exams do not require training classes.
The Q/ISP certification is selected to be reviewed for 8570 certification list & awaiting NOCA's new assessment based certification approval.
What is a "Qualified" Q/ISP?
A Qualified Q/ISP has attained 4 SU Q/ISP® Validation Certifications. Each Validation Certification is attained by attending the Q/ISP tactical security skills certification prep class to validates your tactical security skills - Q/EH, Q/SA - Q/PT License, Q/FE & Q/ND. Each validation & certification prep class is 5 days of hands-on labs, with an online certification exam AND a intense hands-on "Practical" exams. You have to pass both the On-line certification exam and the "Practical" validation projects before you earn a SU Q/ISP (Validation) Certification.
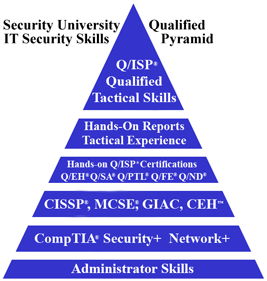
The Security University Security Pyramid represents enlightenment, man's breaking free of stagnant education and reaching towards the supreme source of security skills training and validation, globally illuminating risk preparedness.
Prior to 2008, if you attended Security University's EC-Council® Authorized CEH®, ECSA®,CHFI® classes and passed the exams you are eligible for the Q/ISP® Qualified Certifications but still have to pass the Q/ISP certification exam.
Since 2004 SU has certified over 3500 ECSA™/ Q/SA® Qualified Security Analysts Penetration Testers in 7 countries!
Customize your Q/SA® Q/PTL training program today!
![]() US Congress wants hack teams for self-penetration download for more..
US Congress wants hack teams for self-penetration download for more..
Compliance requirements aside, penetration testing is an absolutely critical aspect of any security program. Attackers test every company's defenses every day.
Legal Notice:
The ECSA™/LPT™ Certification is provided exclusively by EC-Council® and its ATC's, Security University is not sponsored by, approved by, or affiliated in any way with EC-Council.